Backup and Recovery
Overview
The Fireblocks Non-Custodial Wallet (NCW) provides a backup and recovery mechanism to make sure that users can recover their keys even if their NCW device is lost or damaged.
The Fireblocks NCW feature allows the end-user key share on the device to be backed up. When initiating the backup, the SDK generates a random symmetric encryption key. The key share is then encrypted using this key and stored on Fireblocks servers. The encryption key can then be backed up in various ways, from downloading it to the user's computer or placing it on the user's iCloud or Google Drive using end-user authentication.
Upon recovery, the encrypted key share is fetched from Fireblocks servers, and assuming the end-user provides the correct encryption key, the recovery will be successful.
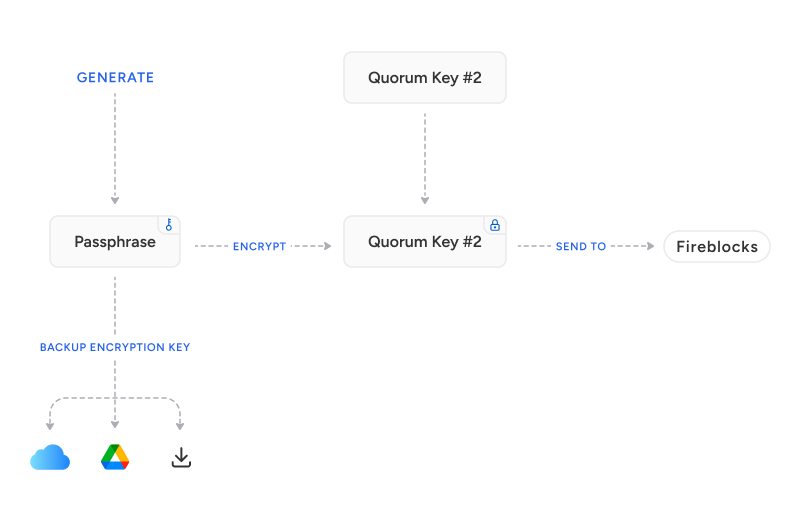
Backup and recovery procedure
NoteThese steps only apply to the following NCW versions:
- Android / iOS SDK: 2.1 and later
- JavaScript SDK: 10.0 and later
A safe backup and recovery procedure is crucial, as this is how you provide your clients with a safe environment to manage their wallets, even if they were to lose a device.
Below are our guidelines for backup and recovery procedures for your NCWs.
Backup
Please note that steps 1 and 2 are under your implementation, while step 3 calls the Fireblocks SDK backup.
- Save the
passphraseand thepassphraseIdon your preferred user cloud, such as iCloud or Google Drive. passphraseIdshould be a GUID (It is enforced by Fireblocks).- In your backend proxy database, save the
passphraseIdand the path to thepassphrase. This should indicate which user cloud you used and the path to the passphrase. - Call the Fireblocks implementation for backup together with the
passphraseand thepassphraseId.
Recovery
- Call the SDK's
recoverKeysfunction with a callback that implements a function that, when given apassphraseId, will fetch the associated passphrase for the user. - The Fireblocks SDK fetches the last encrypted key share with the associated
passphraseIdand then uses your callback to decrypt the key share locally.
Updated 4 months ago