High-Level Architecture
Overview
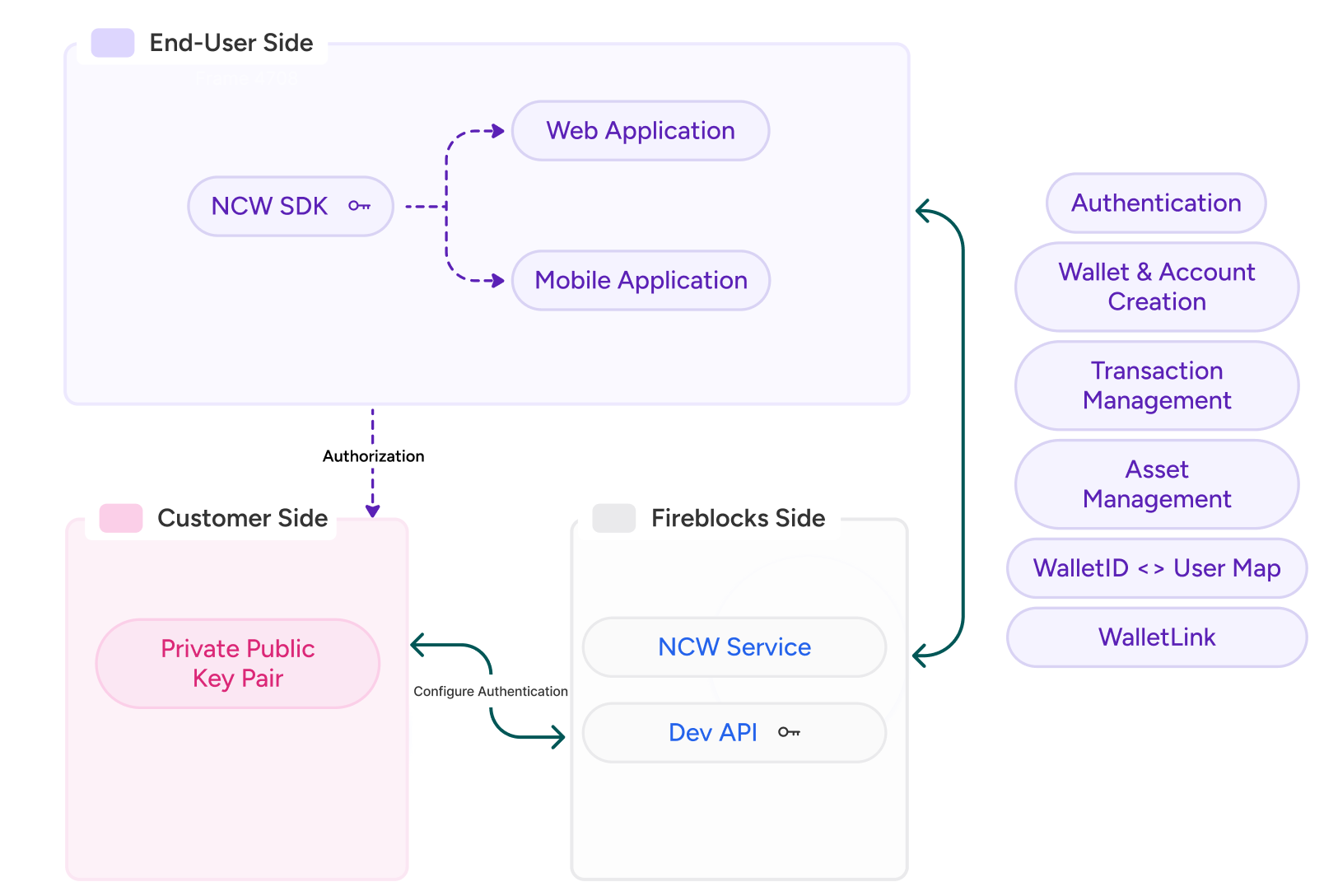
The Fireblocks Embedded Wallet (EW), formerly Non-Custodial Wallet (NCW), architecture is designed with a minimalistic approach to provide maximum flexibility and ease of use.
Fireblocks provides Android, iOS, and Web SDKs for easily integrating EW functionality into your mobile and web applications. The mobile and web SDKs focus solely on MPC key provisioning, signing, and backup/recovery.
Integration Components
There are two main components required for integrating the Fireblocks EW feature:
- Client-side application: A mobile or web app with the EW SDK implemented.
- Fireblocks: An EW-enabled workspace.
The current architecture uses a client-only approach, where the SDK communicates directly with Fireblocks APIs — no backend server is required.
Optional: Backend Proxy Server
In the current architecture, a backend server is not required. However, some customers may choose to implement a backend proxy server for advanced use cases like request validation, rate limiting, or additional business logic.
Learn more about backend proxy integration
Example of EW creation
- create a wallet (assign) ->
ew.assignWallet()
- The client SDK calls the
assignWallet()method, which communicates directly with Fireblocks to create the wallet if it doesn't exist yet. - The client application can store the wallet ID and continue with other wallet operations.
Updated 4 months ago